Getting Started with OAuth 2.0: A Beginner's Guide to Seamless Access and Security
Have you ever found yourself signing up for a new app, only to be greeted with the option to log in using your trusted Gmail, Facebook, or LinkedIn credentials? It's a convenience we often take for granted, seamlessly hopping between platforms without the hassle of creating yet another username and password combination. But have you ever wondered about the magic behind this seemingly effortless process?

Today, we will embark on a journey to unravel the intricacies of the technology that powers this seamless authentication and authorization experience. Before we plunge into the depths of OAuth 2.0, let's first understand the fundamental concepts of authentication and authorization.
Authentication: The Gateway to Your Digital Identity
Authentication involves verifying the identity of a user by obtaining credentials, such as a username-password combination ensuring that only the rightful owners gain access. Essentially, it's the process that confirms you are who you claim to be.
Authorization: Navigating the Permissions Maze
Once authenticated, the journey continues into the realm of authorization. Authorization determines the permissions an authenticated user has within the system, controlling what resources they can access.
And now, the star of our show: OAuth 2.0
OAuth, short for Open Authorization, is the maestro orchestrating the symphony of authorization. Ever logged into an app using your Google or Facebook account, marveling at the absence of the password hassle? That's OAuth at work.
How? Let's break it down.
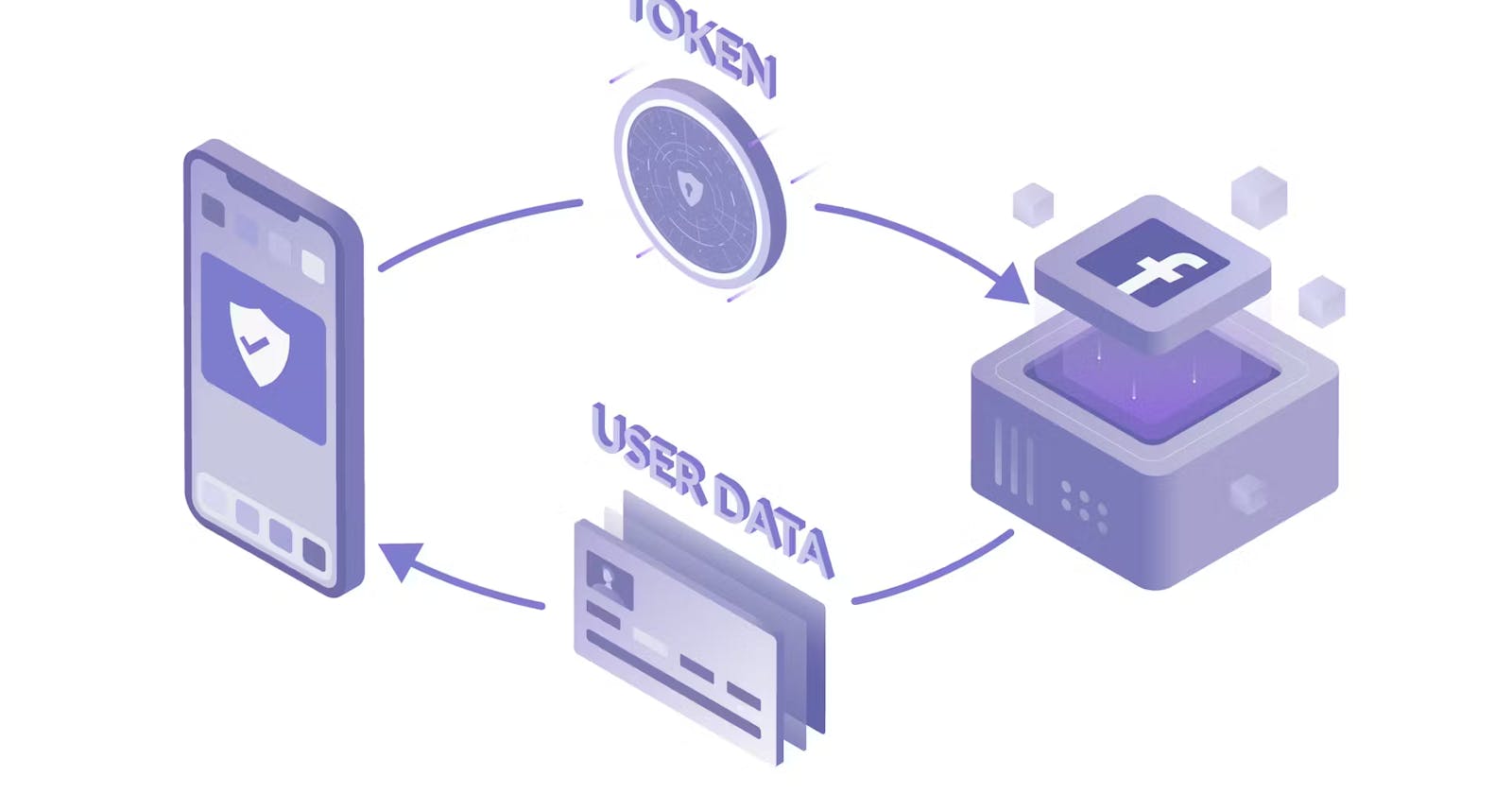
OAuth operates on the concept of access tokens. When you authenticate yourself on a third-party website using, let's say, your Google account, the Google authorization server issues an access token to that website—with your approval, of course. This token becomes the golden key, granting the website access to your data hosted on the resource server. Your Gmail inbox, contacts, photos—these are the resources that can be tapped into by any third-party application with your consent.
Why OAuth?
In a world teeming with digital interactions, OAuth simplifies the process of logging in and sharing data across platforms. It's a passport that allows you to traverse the internet without the burden of remembering multiple passwords. More importantly, it's a secure and efficient way for you to grant controlled access to your digital treasures.
So, join me on this exploration of OAuth 2.0, where we will unravel the mysteries of access tokens, resource servers, and the secure dance of authorization. It's not just technology; it's the key to a safer, more interconnected digital realm. Get ready to explore the wizardry that enables you to grant access without compromising your castle's secrets. Welcome to the world of OAuth – where convenience meets security in the dance of digital authorization.
Emergence of OAuth 2.0?
In the bustling realm of the internet, where millions of users navigate through a labyrinth of applications, a need arose to simplify the way data is shared and accessed across these virtual landscapes. Enter the protagonist of our tale: OAuth 2.0, a groundbreaking protocol that changed the rules of the game and brought a new level of security to the interconnected web.
Picture the early days of the internet, where users had to share their most coveted possession—their passwords—with every application they wanted to use. It was like handing out keys to your digital kingdom without much thought. This process not only risked the security of personal data but also left users with a lingering unease about who held the keys to their virtual castles.
Then, in the year 2007, a collective of brilliant minds embarked on a quest to revolutionize this digital landscape. They formed a community effort that would later evolve into OAuth. The goal? To create a system where users could share access without revealing their sacred passwords, and where the scope of access was precisely defined.
The plot thickened as OAuth matured into a standard, finding its home under the watchful eye of the Internet Engineering Task Force (IETF). This consortium of tech wizards meticulously crafted a token-based authorization mechanism, transforming the way users interacted with applications.
Consider this: in the pre-OAuth era, if you wanted a new app to fetch your data from an existing one, you'd have to spill the beans—your username and password. Imagine the vulnerability! OAuth stepped in like a digital guardian, introducing tokens as virtual keys. Now, users could grant access without exposing their secret passcodes.
And the beauty of OAuth lies not just in the access it grants, but in the precision of that access. Users could now define specific scopes, determining which corners of their digital realm were accessible. No more oversharing—just the right amount of information for a seamless, secure experience.
But the real stroke of genius? The power to revoke access. If a once-trusted app turned rogue, users could yank its virtual key, instantly shutting it out from their digital kingdom. It was a game-changer, putting users in the driver's seat of their own data.
So, as you traverse the vast expanse of the internet today, remember the journey of OAuth 2.0. From the insecure days of sharing passwords like candy to a world where tokens act as guardians, ensuring your digital secrets are safe. The evolution of OAuth is a testament to the ever-growing quest for security and privacy in the dynamic realm of cyberspace.
Simplified OAuth 2.0 Process for End Users:
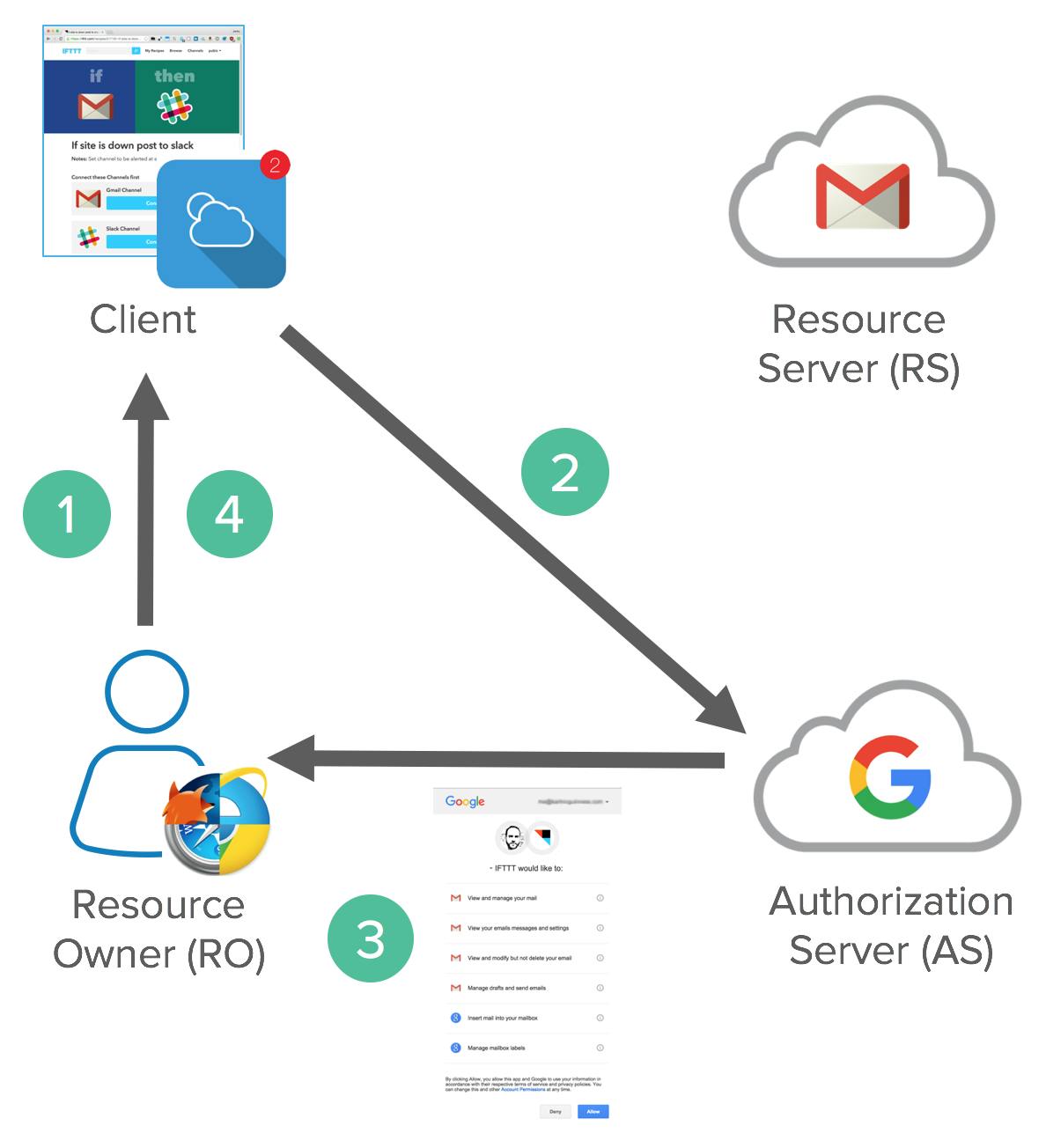
Let's consider a scenario involving a music streaming service (client) seeking access to a user's playlists and song history stored on a social media platform (resource server). The authorization server acts as an intermediary to facilitate this access without the client directly obtaining the user's credentials.
Resource Owner (User): The user is the owner of playlists and song history on the social media platform. They want to use a music recommendation service, which is the client, to enhance their music experience.
Client (Music Recommendation Service): The music recommendation service is the third-party application (client) that seeks access to the user's playlists and song history on the social media platform.
Authorization Server (Social Media Platform): The social media platform serves as the authorization server. It plays a central role in facilitating the authorization process. It issues access tokens to the client after the user successfully authorizes the request.
Resource Server (Social Media Platform): The social media platform's server hosts the protected resources, such as the user's playlists and song history. It is responsible for handling requests for access to these resources using the access token obtained during the authorization process.
Here's how the OAuth 2.0 workflow would unfold in this example:
The music recommendation service (client) requests access to the user's playlists and song history on the social media platform (resource server).
The user is redirected to the social media platform's login page, where they enter their username and password. The credentials are not shared with the music recommendation service (client).
Upon successful login, the user is presented with a screen displaying the specific data (playlists and song history) that the music recommendation service (client) is requesting access to. The user consents to this scope.
The social media platform's authorization server generates an authorization code and provides it to the client.
The client uses the authorization code to request an access token from the authorization server.
The authorization server validates the authorization code and, upon successful validation, issues an access token to the client.
The client then uses the access token to make requests to the resource server (social media platform) for the user's playlists and song history.
The resource server verifies the access token with the authorization server. If the access token is valid, the resource server grants the client access to the user's playlists and song history.
This process ensures that the user's credentials are not shared with the client, and the client can access the user's data on the resource server within the specified scope.
What is the significance of using OAuth 2.0 :
User-Friendly Authentication: OAuth 2.0 enables a user-friendly authentication process. Users log in only on the social media platform's login page, reducing the risk associated with sharing credentials across multiple services. This ensures a seamless and secure experience for users.
Granular Authorization: OAuth 2.0 allows for granular authorization. In our example, the user sees exactly what data the music recommendation service is requesting (playlists and song history) and can grant or deny access to each specific resource. This fine-grained control enhances user trust and privacy.
Client-Side Security: The music recommendation service (client) never sees or handles the user's credentials. OAuth 2.0 eliminates the need for the client to store or manage sensitive information, reducing the risk of unauthorized access or data breaches.
Standardization and Interoperability: OAuth 2.0 is a widely adopted industry standard, promoting interoperability between different platforms and services. Developers can implement OAuth 2.0 for their applications, knowing that it is a proven and widely supported authorization framework.
Scalability: OAuth 2.0 is scalable for various application types and use cases. Whether it's a web-based music streaming service, a mobile app, or an Internet of Things (IoT) device, OAuth 2.0 provides a flexible and scalable solution for secure authorization.
Revocation of Access: If at any point the user decides to revoke access to their playlists and song history, OAuth 2.0 provides mechanisms for token revocation. This empowers users to control and manage access to their data.
Developer Trust and Integration: Developers can leverage OAuth 2.0 to build applications that integrate with established platforms securely. The standardized protocol fosters trust between users, clients, and resource servers, contributing to a positive developer ecosystem.
In summary, OAuth 2.0 offers a secure and standardized framework for authorization, ensuring that developers can build applications that access user data in a controlled and user-friendly manner. The protocol's emphasis on security, user consent, and interoperability makes it a fundamental tool for developers aiming to provide secure and seamless access to protected resources.
How are access tokens different from refresh tokens in OAuth?
Access Tokens: These are tokens issued by the authorization server that grant access to specific resources on behalf of a user. They are typically short-lived and are used by the client to authenticate and access the user's data on the resource server.
Refresh Tokens: Refresh tokens are credentials used to obtain a new access token when the current one expires. They have a longer lifespan than access tokens and provide a way for the client to maintain continuous access without requiring the user to reauthenticate.
Imagine you have a concert ticket (access token) that allows you access to a concert (user's data). This ticket has an expiration time, say three hours. Instead of going back to the ticket booth every three hours to get a new ticket, you have a backstage pass (refresh token) that, when shown before your ticket expires, allows you to get a new ticket without leaving the concert venue.
In this analogy: Access Token (Concert Ticket): Grants you access to the concert (user's data) for a limited time. Refresh Token (Backstage Pass): Allows you to get a new ticket (access token) without going through the initial ticket purchase process (user reauthentication).
What challenges and recommended best practices should developers and end users be aware of when utilizing OAuth 2.0?
Challenges:
Scope of Authorization:
Developer: Determining the appropriate scope of authorization can be challenging. Overly broad scopes may lead to unnecessary access, while too narrow scopes may limit the functionality of the client.
End User: Users may find it confusing to understand and manage the scopes they are granting, risking unintentional exposure of sensitive information.
Token Management:
Developer: Handling and securely storing tokens, both access and refresh tokens, requires careful consideration to prevent security vulnerabilities.
End User: Users might be concerned about the security of tokens and how they are managed by both the client and authorization server.
Token Expiry and Refresh:
Developer: Managing token expiration and refreshing tokens seamlessly without disrupting user experience can be complex.
End User: Users may find it inconvenient if they have to frequently re-authenticate due to short-lived access tokens.
Best Practices:
Clearly Define Scopes:
Developer: Clearly define and document the scopes required by your application. Request only the permissions necessary for the application's functionality.
End User: Understand and review the requested scopes during authorization to ensure you are comfortable with the access being granted.
Secure Token Handling:
Developer: Implement secure practices for token storage and transmission. Use HTTPS, store tokens in secure locations, and employ best practices for token management.
End User: Be aware of the security measures implemented by the application regarding token handling to ensure the protection of your data.
User-Friendly Authorization Process:
Developer: Design an authorization process that is user-friendly and transparent. Clearly communicate the purpose of the requested permissions.
End User: Take the time to understand what permissions are being requested and why. Only grant access to applications you trust.
Conclusion
OAuth 2.0 stands as the guardian of a more secure and interconnected digital realm. It has transformed the landscape of user authentication and authorization, offering a seamless experience for individuals navigating the vast expanse of the internet.
OAuth 2.0, when implemented correctly, provides a powerful framework for secure and delegated access. Developers should prioritize clear documentation, secure token handling, and user-friendly experiences. End users, in turn, should be proactive in understanding the permissions they grant and choose applications with strong security practices. Striking a balance between functionality and security is crucial for a successful and trustworthy OAuth 2.0 implementation. Ongoing education and communication between developers and end users are key to addressing challenges and ensuring a positive experience for all parties involved.